Reproduced here from the ISACA GWDC Blog
White House Releases Draft Federal Zero Trust Strategy
This week, the White House released their Federal Zero Trust Strategy to help agencies comply with Executive Order 14028. If you’re not familiar with Executive Order 14028, it sets the following federal security direction.
- Remove barriers to sharing threat information.
- Modernize federal cybersecurity by prioritizing adoption and use of cloud technology and zero trust implementation planning.
- Enhance software supply chain security.
- Establish a cyber safety review board.
- Standardize the Federal Government’s Playbook for responding to cybersecurity vulnerabilities and incidents.
- Improve detection of cybersecurity vulnerabilities by deploying an Endpoint Detection and Response (EDR) initiative.
Federal Zero Trust Strategy
The Federal Zero Trust Strategy, which is open to public comment until September 21, the purpose is to put all Federal agencies on a common roadmap toward a highly mature zero trust architecture. It sets specific zero trust goals to achieve by the U.S. government fiscal year 2024. The goals align with the five zero trust pillars of the identity, device, network, application, and data. Each Federal agency must have an agency plan that aligns with this strategy. The Cybersecurity and Infrastructure Security Agency (CISA) also published two additional documents; a Zero Trust Maturity Model and a Cloud Security Technical Reference Architecture.
Zero Trust Maturity Model
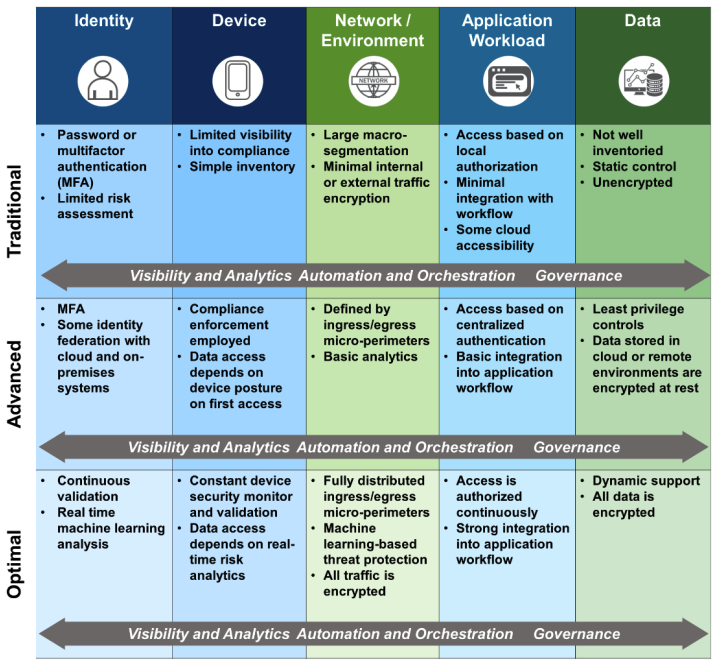
The Zero Trust Maturity Model, which is open to public comment until October 1, supports the continued evolution of CISA’s programs and capabilities within a rapidly changing environment and technology landscape. It focuses on three levels of maturity from traditional to optimal along the five zero trust pillars.
DHS CISA Zero Trust Maturity Model from federal zero trust strategy. Image courtesy of the DHS CISA Zero Trust Maturity Model. CISA designed this maturity model to help modernize its current cybersecurity programs and services fully functional with cloud-computing environments with zero trust architecture. While CISA created it for their programs, anyone can use the model to help plan or inform security architecture decisions and capabilities. CISA also released a Cloud Security Technical Reference Architecture.
Cloud Security Technical Reference Architecture
The Cloud Security Technical Reference Architecture, which is open to public comment until October 1, illustrates recommended cloud migration and data protection approaches outlined in Executive Order 14028. It touches on topics like FedRAMP, cloud migration strategies and scenarios, and cloud security posture management. It also contains a section on developing a DevSecOps mentality and building a scalable, repeatable architecture that is highly available and resilient to deliver the best digital services.
All three documents, including the draft Federal Zero Trust Strategy, are open to comment through September 21 or October 1.