Kenneth Myers
School of Technology and Business
Marymount University
April 11, 2021
Literature Review Structure
Table of Contents
- Literature Review Mind Map
- Literature Review Argument Steps
Step 1 - Majority of breaches use an IAM process as an attack vector
Step 2 - IAM processes are implemented using cybersecurity frameworks
Step 3 - Cyber frameworks are used to build cybersecurity workforce models
Step 4 - Cybersecurity workforce models do not identify specific IAM roles
Step 5 - Specific IAM roles are needed to reduce breaches exploting an IAM process - Literature Review Section Structure
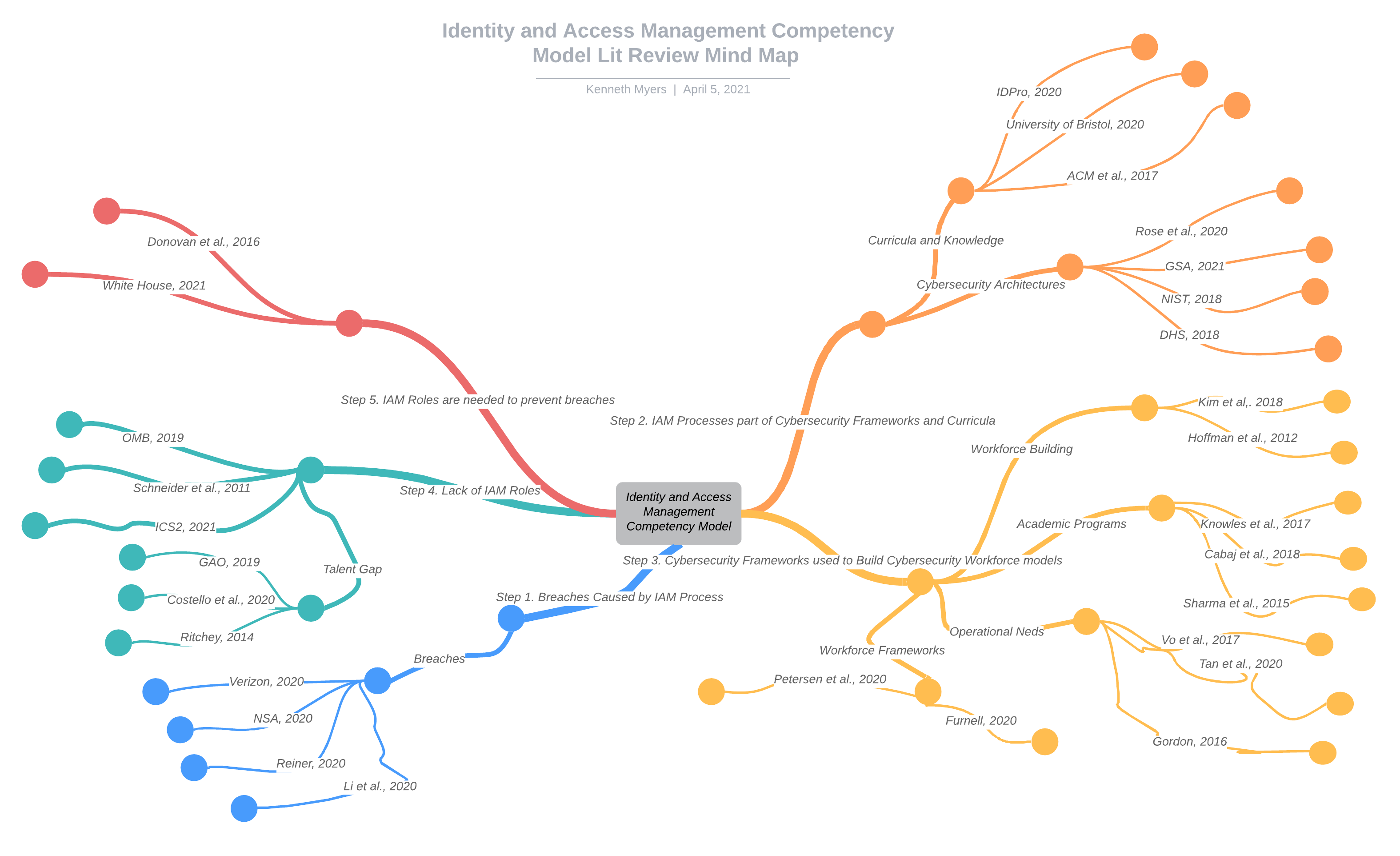
Literature Review Mind Map
Mind map depicting my literature review structure generated with LucidChart.
Literature Review Argument Steps
Step 1
A majority of breach attack vectors exploit an identity and access management (IAM) processes.
| Argument Steps | Relevant References |
|---|---|
| Breaches caused by identity processes | Verizon, 2020; NSA, 2020; Reiner, 2020; Li et al., 2020 |
| Adversary Tactics and Techniques | MITRE, 2021 |
Step 2
Identity and access management processes are implemented using a cybersecurity framework.
| Argument Steps | Relevant References |
|---|---|
| Cybersecurity Curricula | University of Bristol, 2020; ACM et al., 2017 |
| IAM Knowledge and Terms | IDPro, 2020 |
| Cybersecurity Architecture | Rose et al., 2020; GSA, 2021; NIST, 2018; DHS, 2018 |
Step 3
Cybersecurity frameworks are used to build cybersecurity workforce models.
| Argument Steps | Relevant References |
|---|---|
| Workforce Building | Kim et al., 2018; Hoffman et al., 2012 |
| Academic Programs | Knowles et al., 2017; Cabaj et al., 2018; Sharma et al., 2015 |
| Operational Needs | Vo et al., 2017; Tan et al. 2020; Gordon, 2016 |
| Workforce Frameworks | Petersen et al., 2020; Furnell, 2020 |
Step 4
Cybersecurity workforce models identify IAM tasks spread across multiple roles, but do not identify specific IAM roles.
| Argument Steps | Relevant References |
|---|---|
| Importance of IAM Processes | Schneider et al., 2011; OMB, 2019; ISC2, 2021 |
| Talent Gap | GAO, 2019; Costello et al., 2020; Ritchey, 2014 |
Step 5
Specific IAM roles are needed to reduce breaches exploiting an IAM process.
| Argument Steps | Relevant References |
|---|---|
| IAM Workforce Strategy | Donovan et al., 2016; White House, 2021 |
Literature Review Section Structure
2.0 Literature Review
2.1 Literature Synopsis
2.2 Adversary Tactics, Techniques, and Common Attack Vectors
2.3 Defend Against Attacks using Cybersecurity Frameworks
2.4 Build your Cybersecurity Team
2.4.1 Align your Cybersecurity Team with your Cybersecurity Framework
2.4.2 Define Specific Roles for Each Major Framework Area
2.4.3 Align Adversary Tactics and Techniques to Responsible Roles
2.5 Research Contributions